Physical security
Physical security should be a key part of our data security and defense architecture. Application controls, the essential to physical security, have become a weak defense. It is used to protect the company’s premises, sites, facilities, buildings, people, information, and other assets. Security controls are designed to protect all elements of information systems. Properly designed and managed access controls are at the core of protecting and managing the properties of organizations (Moses and C. Rowe, 2016).
Types of physical security
Physical security is a critical part of an active safety plan. In addition to defending against malicious attacks such as theft vandalism and terrorism, security preparation should also provide defense from natural disasters such as flooding or explosions. ISC(2) suggest that security controls can be
categorized into 6 control types:
Preventative – controls meant to prevent unauthorized actions. Examples of preventive controls would include, locks, biometrics, mantraps, etc
Detective – controls meant to send alerts during or after an attack. Examples of detective controls would include job rotation, mandatory vacations, recording and reviewing security cameras. Corrective – controls meant to restore systems to normal after unwanted or unauthorized activity. These normally only have limited capability to respond without user interaction. Examples include antivirus solutions, intrusion detection systems, and business continuity planning.
Recovery – controls meant for after a security incident has occurred. Recovery controls are meant to restore the functionality of the system and organization. Examples include reinstallation of Operation Systems and data restored from backups.
Deterrent – controls meant to discourage actions. Examples include “Beware of Dog” or “SecuritySystem” signs.
Compensating – These provide a supplementary or alternative solution to a control that is too expensive or difficult to implement.
categorized into 6 control types:
Examples of threats
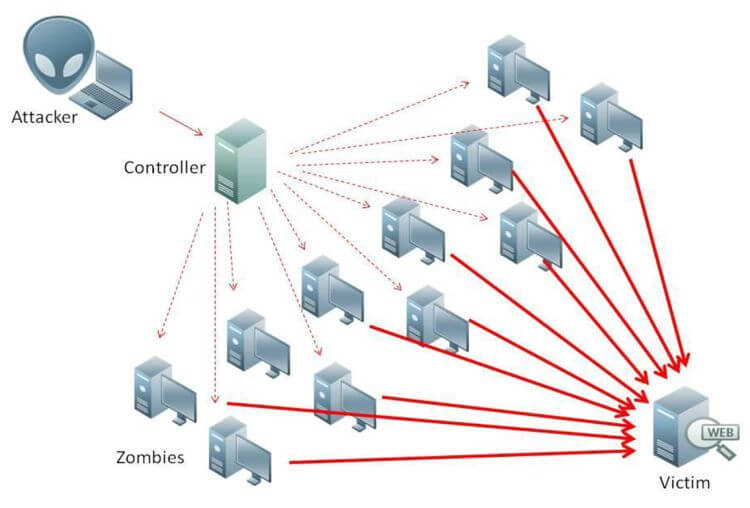
Threats can come in a large number of forms and shapes. Hackers are ingeniously and they always are looking for a breach in security, to make any of the actions listed below
Impact on organization due to lack of physical security
The good news is that the topic of physical security can be easily integrated into a larger security awareness training program. To help employees understand their role in maintaining a safe and secure work environment, educate them on key components of physical security and train them to follow best practices that will help them keep your people, areas, and assets secure. In addition to interactive education, use reinforcement tools like posters, articles, videos, and other security awareness materials to keep physical security top-of-mind for companies end-users
Conclusion
Administrative, technological and physical checks properly carried out allow the company to manage and protect its capital. Such controls should have an in-depth security approach that works together to provide multiple layers of protection if regulation is bypassed. Security measures help dissuade, reject, track, and then prevent threats from accessing information.
Threats can come in a large number of forms and shapes. Hackers are ingeniously and they always are looking for a breach in security, to make any of the actions listed below
- taking control of the door lock system to open doors and gates during a robbery
- turning off video recording and monitors to allow a thief to come unnoticed into a building
- removing records from the security management system, thus removing the evidence of a crime
- taking control of CCTV systems to guide an intruder through the building
- monitoring CCTV cameras to know when the most money is in the bank, thereby finding the optimal time for a robbery
- monitoring CCTV cameras to get details when people enter PIN codes
- monitoring CCTV cameras to know when security personnel are not present in key areas
- turning off complete physical security systems, leaving security personnel without tools for monitoring and response
- instigating false alarms in order to occupy security personnel, leaving key areas unprotected
Impact on organization due to lack of physical security
- Increase of Theft and Vandalism, without physical security, companies are under risk. There could take place thefts and vandalism.
- No Procedure to Handle Incidents, just as more robberies will take place without protection, there will also be more accidents that put the business at risk, particularly without any kind of protocol to deal with the issue. Find a more serious offense on the house. The problem will quickly escalate without personnel security officers or surveillance systems to avoid the incident, or even to provide proof afterward.
- Business reputation: continued fraud or lack of security for public safety, better consumers will be searching for another place to visit. People feel safer when the buildings seem to have the latest technology. People will be running companies that they trust, and this is a key way to do this.
- Legal Liability: it is essential to have proper security in place to protect the personal information of customers, clients, and vendors. Necessary security not only protects customers but also protects businesses from legal damage that can be costly or potentially shut down. Take steps to protect the data and the personal security of all these individuals and companies in order to improve security and minimize liability.
The good news is that the topic of physical security can be easily integrated into a larger security awareness training program. To help employees understand their role in maintaining a safe and secure work environment, educate them on key components of physical security and train them to follow best practices that will help them keep your people, areas, and assets secure. In addition to interactive education, use reinforcement tools like posters, articles, videos, and other security awareness materials to keep physical security top-of-mind for companies end-users
Conclusion
Administrative, technological and physical checks properly carried out allow the company to manage and protect its capital. Such controls should have an in-depth security approach that works together to provide multiple layers of protection if regulation is bypassed. Security measures help dissuade, reject, track, and then prevent threats from accessing information.
External safeguards provide security protection, motion detectors, and intrusion alarms. Electronic safeguards include smart cards used for access control, physical security devices for intrusion detection, guards and CCTV systems. Physical security is not always the first thing when it comes to safety. Most organizations tend to focus on more technical aspects of threat counteraction. Both network intrusion detection systems and firewalls are completely useless if someone can get to the router and hack the data or the computer. Every company should think, how important is physical security.
References List:
Jentes, A. 2018. Physical Security Risks: Are Your End Users an Asset or a Liability?. [online].
Available at: <https://www.proofpoint.com/us/security-awareness/post/physical-security-risks-are-your-end-users-asset-or-liability> [Accessed on 3rd March 2020]
Available at: <https://www.proofpoint.com/us/security-awareness/post/physical-security-risks-are-your-end-users-asset-or-liability> [Accessed on 3rd March 2020]
Moses, S. and C. Rowe, D., 2016. Physical Security and Cybersecurity: Reducing Risk by Enhancing Physical Security Posture through Multi-Factor Authentication and other Techniques. International Journal for Information Security Research, 6(2).
Zenitel.com. 2020. Are You Aware Of The Threats To Your Physical Security System?. [online] Available at: <https://www.zenitel.com/news/are-you-aware-threats-your-physical-security-system> [Accessed 2 March 2020].
Zenitel.com. 2020. Are You Aware Of The Threats To Your Physical Security System?. [online] Available at: <https://www.zenitel.com/news/are-you-aware-threats-your-physical-security-system> [Accessed 2 March 2020].