First case study- Apple phone and its security.
Have Apple any issue regarding its security? It's any possibility to access Apple devices?
I put my self some questions after I hard a university teacher, which said,, We can access an Apple device, accessing first a smart device which is connected with the Apple device. As an Android user, I will study both android and iOS systems. In addition, I want to find out if Apple company will convince me to buy its devices or I will be using the Android system. For the case study regarding the Android system, I will study about the Samsung company. Samsung is a loyal competition for the Apple company.

Apple, iOS.
The first iPhone was launched in 2007 by Steve Jobs. That rapidly became one of the most widely discussed consumer products ever. With a brand like a computer screen touch screen, thousands of customers race to be the first to purchase the device, including computers and Wi-Fi connectivity. Opponents have been quick to launch phones for similar features.
According to Apple, the company is using hardware security, antivirus software is building into hardware. It has security competences designed into silicon. This kind of security is found in any Apple products which running iOS, iPadOS, macOS, watchOS, and tvOS (Apple Support, 2020).As I said, I choose to study the iPhone device's security.
The most critical component is the Secure Enclave, which is built into modern devices. Secure Enclave is a type of cryptography. The enclave provides a foundation for encrypting data, secure boot in macOS and biometrics.
About Secure Enclave:
Secure Enclave is a hardware-based key manager isolated from the main processor that provides an extra layer of security.
If the devices have been compromised, the Secure Enclave maintains the integrity of its cryptographic operations.

Fig1. The Secure Enclave processor
Review
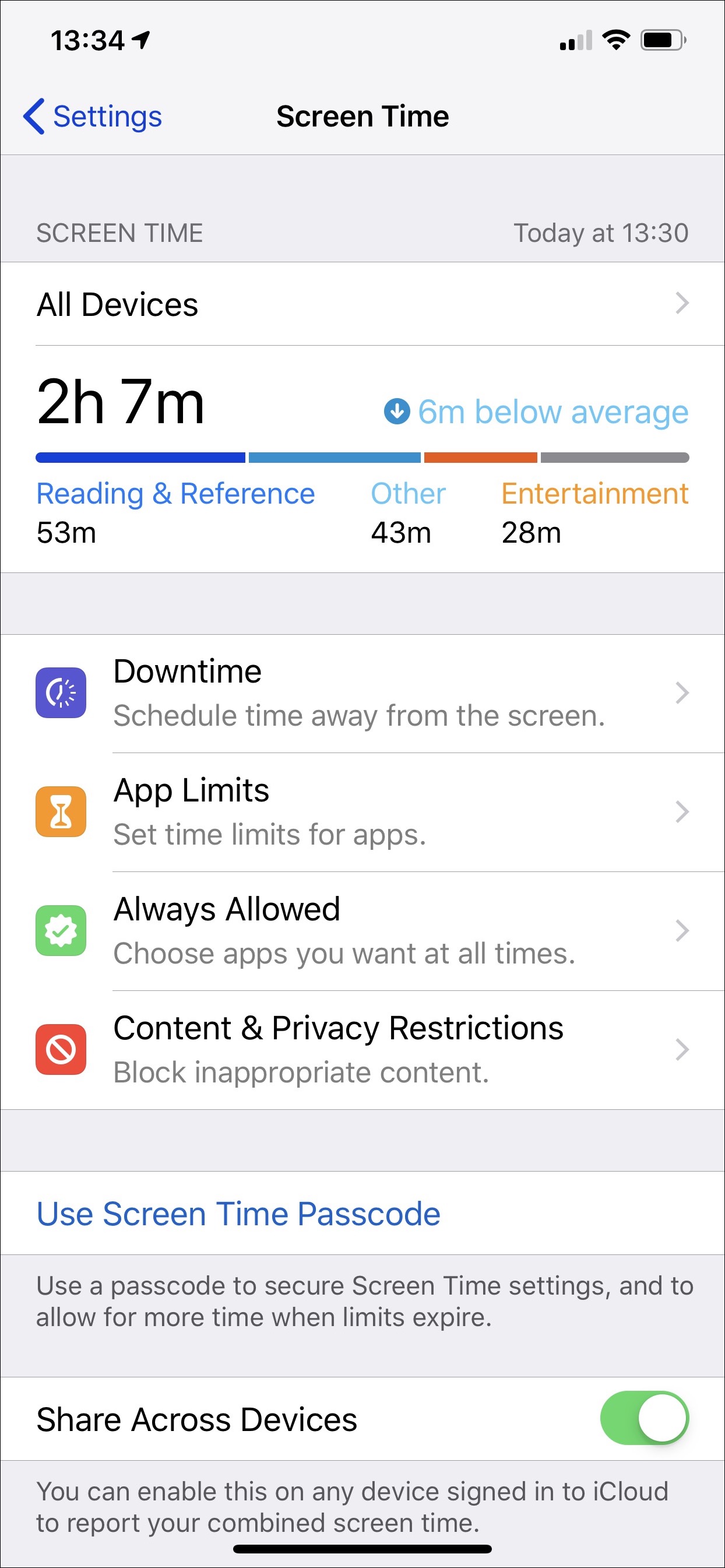
Due to their security, Apple imposed the customer restricted access, for example, to download software from unknown sources. Apple focuses on absolute control of all elements of its product from the software all the way down to the hardware. But this makes for much better software support on the positive side and a better overall experience. However, Apple offers some restrictive futures which help the customer to stay safe. One of these features is the Parental controls app: such settings offer various ways of preventing children from consuming inappropriate content. This app coming with features such as Screen Time, a feature that Apple has introduced to iOS 12, reveals how much time a customer spending on his iPhone or iPad, for example, pale if the customer wants to know how much time spend on Facebook, Instagram or playing games. Furthermore, the Screen Time app contains another setting in which parents can enable them to reach children from inappropriate content and managing their time.
from: McElhearn, K. (2020)Although they have built strong security which believed is impenetrable they have a breach in the security system. According to CVE Details, who has noticed that in 2019, iOS contains 1655 vulnerabilities in the security system, most of the latest vulnerabilities are related to the Bluetooth BR / EDR and multiple memory corruption issues (Cvedetails.com, 2020).
According to Matthews (2019), a team of researchers at Google in February warned Apple of vulnerabilities that persisted for two years and allowed hackers to install malware on iPhones after people visited specific websites. Although it happens for more than two years, it went public just in February 2019, after Google publish it. They revealed five so-called exploit chains that connect vulnerabilities in security together and allow hackers to move through each layer of security protections built into an operating system (Matthews, 2019).
The exploit chains took advantage of 14 total security vulnerabilities that allowed cybercriminals to gain full phone control after putting malware on it that served as a tracking implant. The cybercriminals set Malware into these sites and infect the iPhones through websites. Researchers have confirmed, thousand of the user were hacked, without being aware of it. Nonetheless, the researchers reported that thousands of visitors were likely to go to those online destinations every week, and since September 2016 the malware existed, and since at least 2017 the impacted sites have been live online (Matthews, 2019). The most vulnerabilities were found in the Apple system iOS 10 to 12. These vulnerabilities have plagued most of Apple's iOS 10 to 12 operating systems, Google information also discusses how cybercriminals have made a "sustained effort" to exploit these vulnerabilities (Matthews, 2019). The researchers at Google did not attempt to accuse or say anything about the groups that organized those attacks. Nonetheless, after the news broke, TechCrunch claimed that its sources claim that the infected websites that contain the malware were actually part of a state-based attack— and possibly one from China (Matthews, 2019). A prediction is related that these attacks will extend to the android system, Forbes state, the individuals who given that data moreover charged that the assaults expanded to Windows and Android frameworks. Be that as it may, Google did not comment on that plausibility (Matthews, 2019).
Google has given the Apple, seven days to fix that issue and come with any further solution to avoid that kind of problem not come in the future. Apple patched the issues and released a security patch six days after hearing about what Google discovered, but the firm hasn't released a statement yet.
Apple fixed this flaw in a patch carried out in Patch 12.1.4
In conclusion, Apple has strong security , however, it can be broke. Therefore, users should not just trust that the security offered by Apple is sufficient to protect them from attack. Regarding the privacy and the possibility to have full freedom, Apple has restricted users access to install any app on the iPhone.
Customers should pay more attention to what Google has discovered, avoid accessing untrusted sites and update their devices
(How Apple security is broken by devices like smart devices?? (Cvedetails.com, 2020) )
References list:
Apple Support. (2020). Hardware security overview. [online] Available at: https://support.apple.com/en-gb/guide/security/secf020d1074/1/web/1 [Accessed 18 Feb. 2020].
Cvedetails.com. (2020). Apple iPhone Os: List of security vulnerabilities. [online] Available at: https://www.cvedetails.com/vulnerability-list/vendor_id-49/product_id-15556/Apple-Iphone-Os.html [Accessed 27 Feb. 2020].
Matthews, K. (2019). Incident Of The Week: Apple iPhones Affected By Data Breach Discovered By Google’s Project Zero Security Researchers. [online] Cyber Security Hub. Available at: https://www.cshub.com/malware/articles/incident-of-the-week-apple-iphones-affected-by-data-breach-discovered-by-googles-project-zero-security-researchers [Accessed 25 Feb. 2020].
McElhearn, K. (2020). iOS 12 Parental Controls and Restrictions: How to protect your kids on iPad, iPhone, iPod touch. [online] The Mac Security Blog. Available at: https://www.intego.com/mac-security-blog/protect-your-kids-on-ios-devices-with-parental-controls/ [Accessed 27 Feb. 2020].
The references are very good and show variety in sources of information. As a case study should include research with in-depth sourcing, but this needs to have some more of your own discussion on the subject too. Don't rely too heavily on paraphrasing and citation.
ReplyDelete