Phishing
Phishing attacks: defending organizations provides a multi-layered set of mitigations to improve your organization's resilience against phishing attacks, whilst minimizing disruption to user productivity.
What is phishing?
Phishing is when attackers attempt to trick users into doing 'the wrong thing', such as clicking a bad link that will download malware, or direct them to a dodgy website.
Phishing can be conducted via text message, social media, or by phone, but the term 'phishing' is mainly used to describe attacks that arrive by email. Phishing emails can reach millions of users directly, and hide amongst the huge number of benign emails that busy users receive. Attacks can install malware (such as ransomware), sabotage systems, or steal intellectual property and money. Phishing emails can hit an organization of any size and type.
An intrusion could have devastating results. For individuals, this includes unauthorized purchases, the theft of funds or the identification of thefts.
In fact, phishing is often used to gain a foothold in corporate or government networks as part of a larger assault, such as an advanced persistent threat (APT) case. In this last scenario, workers become exploited in order to breach security perimeters, spread ransomware inside a closed environment, or obtain unauthorized access to protected data. In addition to increasing market share, reputation, and customer confidence, a company succumbing to such an assault usually sustains significant financial losses.
Phishing attacks
What is a phishing attack
Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers. It occurs when an attacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message. The recipient is then tricked into clicking a malicious link, which can lead to the installation of malware, the freezing of the system as part of a ransomware attack or the revealing of sensitive information.
Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers. It occurs when an attacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message. The recipient is then tricked into clicking a malicious link, which can lead to the installation of malware, the freezing of the system as part of a ransomware attack or the revealing of sensitive information.
An attack can have devastating results. For individuals, this includes unauthorized purchases, the stealing of funds, or identify theft.
Moreover, phishing is often used to gain a foothold in corporate or governmental networks as a part of a larger attack, such as an advanced persistent threat (APT) event. In this latter scenario, employees are compromised in order to bypass security perimeters, distribute malware inside a closed environment, or gain privileged access to secured data.
An organization succumbing to such an attack typically sustains severe financial losses in addition to declining market share, reputation, and consumer trust. Depending on the scope, a phishing attempt might escalate into a security incident from which a business will have a difficult time recovering.
Phishing attack examples describe by Imperva (Learning Center, 2020).
The following illustrates a common phishing scam attempt:
- A spoofed email ostensibly from myuniversity.edu is mass-distributed to as many faculty members as possible.
- The email claims that the user’s password is about to expire. Instructions are given to go to myuniversity.edu/renewal to renew their password within 24 hours
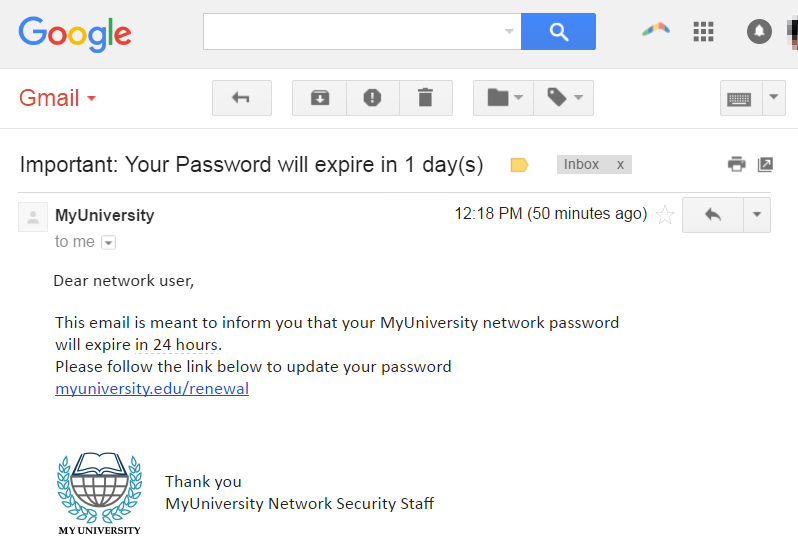
Several things can occur by clicking the link. For example:
- The user is redirected to myuniversity.edurenewal.com, a bogus page appearing exactly like the real renewal page, where both new and existing passwords are requested. The attacker, monitoring the page, hijacks the original password to gain access to secured areas on the university network.
- The user is sent to the actual password renewal page. However, while being redirected, a malicious script activates in the background to hijack the user’s session cookie. This results in a reflected XSS attack, giving the perpetrator privileged access to the university network.
Phishing attack security requires all consumers and companies to take action. Vigilance is important to consumers. A spoofed message also includes small errors that expose its true identity. These may involve spelling errors or domain name shifts, as seen in the URL illustration above. Users should also stop and think about why they're getting such a text.
Learning Center. (2020). What is phishing | Attack techniques & scam examples | Imperva. [online] Available at: https://www.imperva.com/learn/application-security/phishing-attack-scam/ [Accessed 3 Feb. 2020].
Ncsc.gov.uk. (2020). Phishing attacks: defending your organization. [online] Available at: https://www.ncsc.gov.uk/guidance/phishing [Accessed 3 Feb. 2020].

Same thing here Alina, you need to make sure that you are putting some of your own response into the blog posts. What have you learned from this? Can you find other examples and link them to this research?
ReplyDelete