Car hacking
Are autonomous cars more vulnerable to cyber-attacks?
Recently, autonomous vehicles (AVs) are attracting a great deal of attention. We are required to assist/replace human drivers in maneuvering the car, thereby reducing the likelihood of human error-induced road accidents as a means of improving road safety (Cui et al., 2019). In addition, AVs can communicate with other cars, facilities, and pedestrians, as they have activated with the vehicle to everything (V2X) communication technology (Cui et al., 2019).
Car hacking is still a major problem these days. Progress is being made by automakers and manufacturers in defending cars from cyber attacks, but the car-hacking threat is still real and could become even more serious in the future as driverless vehicles start talking to each other.
Fig 1.Model cars run in a city miniature at the Elektrobit booth to show how software for highly automated driving works during CES 2018 on January 9, 2018, in Las Vegas, Nevada.
A worst-case scenario would be hackers who penetrate a vehicle through a minor unit, such as an infotainment system, then wreak disruption by taking control of the vehicle's door locks, brakes, engine or even semi-autonomous driving features. According to Eu.usatoday.com (2018), such a scenario was shown to be feasible in a 2015 remote hacking demonstration involving a Jeep Cherokee that rocked the industry and prompted Fiat Chrysler Automobiles to send 1,4 million cars and trucks owners of UBS sticks with software patches to.
The major car manufacturers create an organization called the Automotive Information Sharing and Analysis Center, known as Auto-ISAC, to study and discuss the best cybersecurity practices.
Autonomous vehicles (AV) have vulnerabilities due to software that contains a large number of codes. Parkinson et al. (2017) claim Autonomous vehicles (AVs) are vulnerable to many forms of cyber attacks, the fully AV driving software will have over 100 million lines of code, so security problems can not be predicted (Parkinson et al. 2017, cited in Linkov, V et al. 2019).
An example of a cyber-attack against autonomous cars is presented by Linkov, V. et al. in their journal namely, when tire-pressure monitoring systems are under attacker's influence, they can display false readings and mask a frequent reduction in air pressure leakage. An attack on the tilt sensor may cause the car to slow down or start braking because the sensor indicates a steep gradient (Parkinson et al. 2017, cited in Linkov, V et al. 2019).
In-vehicle connectivity and communication with V2X (Vehicle to everything) are crucial to maintaining AV performance.
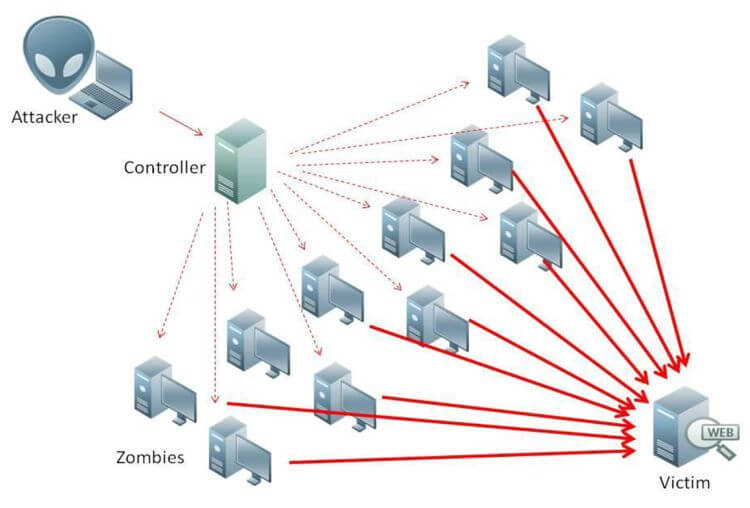
Fig. 2. Potential attacks on AV and AV communication networks. (Cui et al., 2019)
AVs can face different types of attacks, passive or active, external or internal, and malicious or rational. The active attacker sends malicious packets to damage other nodes in the network, while passive attackers frequently check communication within the network to gain useful information, external attackers are generally not authenticated and mostly aim to ruin the system's security and availability, while internal attackers are part of the network and can perpetrate any attackers (Cui et al., 2019).
DoS (Denial of Service) attack is one of the most serious attacks due to the major impact it has on the network connection. Denial of Service (DOS) attack: the main purpose behind a DoS attack is to prevent legitimate organizations from accessing network services and resources; the aforementioned spamming attack and flooding attack are examples of DoS attacks; it can also be called DDOS (Distributed Denial of Service) when several computers and/or internet connexions are used to initiate the attack (Cui et al., 2019). Furthermore, other attacks that could take place are Flooding, Malware, Spamming, Wormhole attacks.
Fig 3. Security attacks on availability and their corresponding countermeasures (Cui et al., 2019).
video: Driverless Cars: A New Challenge to Cybersecurity
The real problem of hacking AVs is when those cars are lost control and they can harm pedestrians or they can even kill car occupants or other AVs drivers. In March 2018 the first fatal AV crash involving a pedestrian was recorded, this raised worldwide attention to the urgent need to ensure AV safety and security in order to prevent the recurrence of such incidents (Cui et al., 2019).
In conclusion, Driverless cars tend to be a significant next step in transport technologies. AVs are a new field that needs more attention and new road rules.AVs are primarily driven by the desire to manufacture quicker, more efficient and safer vehicles. However, AVs also face many outstanding security and safety issues (Cui et al., 2019).
Sources:
Cui, J., Liew, L., Sabaliauskaite, G. and Zhou, F. (2019). A review on safety failures, security attacks, and available countermeasures for autonomous vehicles. Ad Hoc Networks, 90, p.101823
Eu.usatoday.com. (2018). [online] Available at: https://eu.usatoday.com/story/money/2018/01/14/car-hacking-remains-very-real-threat-autos-become-ever-more-loaded-tech/1032951001/ [Accessed 28 Feb. 2020].
Linkov, V et al. (2019). Human Factors in the Cybersecurity of Autonomous Vehicles: Trends in Current Research. Frontiers in Psychology, 10.
The Federalist Society (2018). Driverless Cars: A New Challenge to Cybersecurity. [video] Available at: https://www.youtube.com/watch?v=_YrcslWaUsw [Accessed 1 Mar. 2020].